The global key management systems market is experiencing robust growth, driven by rising demand for enhanced physical security, operational efficiency, and compliance across industries such as healthcare, finance, and critical infrastructure. According to Mordor Intelligence, the Global Key Management Market was valued at USD 1.85 billion in 2023 and is projected to reach USD 3.03 billion by 2029, growing at a CAGR of 8.6% during the forecast period. This expansion is fueled by the increasing adoption of automated solutions that reduce human error, improve auditability, and integrate seamlessly with existing security ecosystems. As organizations prioritize real-time monitoring and access control, automated key management systems have transitioned from niche tools to essential components of modern security infrastructure. In this evolving landscape, leading manufacturers are innovating with IoT-enabled tracking, cloud-based analytics, and biometric authentication to meet heightened security demands. Based on market presence, technological innovation, and scalability, the following ten companies represent the forefront of automated key management system manufacturing worldwide.
Top 10 Automated Key Management System Manufacturers 2026
(Ranked by Factory Capability & Trust Score)
#1 KeyManager – Automated Key Management System
Founded: 2008
Website: keymanager.in
Key Highlights: KEYMANAGER. Leading manufacturer of automated key management solutions. Protecting your assets with innovative technology since 2008. IE. IMPEX ENGINEERING….
#2 Real Estate Digital Solutions Leader
Domain Est. 1988
Website: buildings.honeywell.com
Key Highlights: Supra is a leading provider of mobile credentialing and key management systems, with innovative access solutions for real estate, ……
#3 Encryption Key Management Solutions
Domain Est. 1994
Website: entrust.com
Key Highlights: KeyControl simplifies management of encrypted workloads by automating the lifecycle of encryption keys; including key storage, backup, distribution, rotation, ……
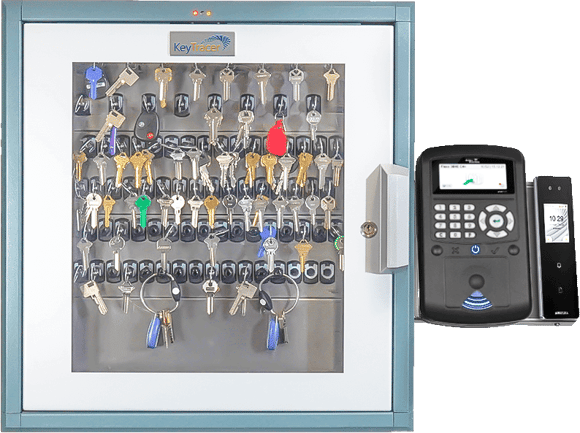
#4 Electronic Key and Asset Control
Domain Est. 1996
Website: keypersystems.com
Key Highlights: The KEYper MX Electronic Key System provides a revolutionary method of key and asset management designed to fit the needs of all industries while providing the ……
#5 Automated Key Distribution for Secure Delivery
Domain Est. 1996
Website: futurex.com
Key Highlights: Futurex’s next-gen automated Key Distribution service secures key delivery to applications and devices, ensuring efficient and error-free key management….
#6 Traka
Domain Est. 1998
Website: traka.com
Key Highlights: Traka’s automated key and equipment management systems are for your organization’s most sensitive assets, bringing better control, visibility and efficiency ……
#7 Real Time Networks
Domain Est. 1998
Website: realtimenetworks.com
Key Highlights: Electronic Key Management System. With our electronic key cabinets, you can manage, track, and secure your facilities and fleet keys. Know where keys are and ……
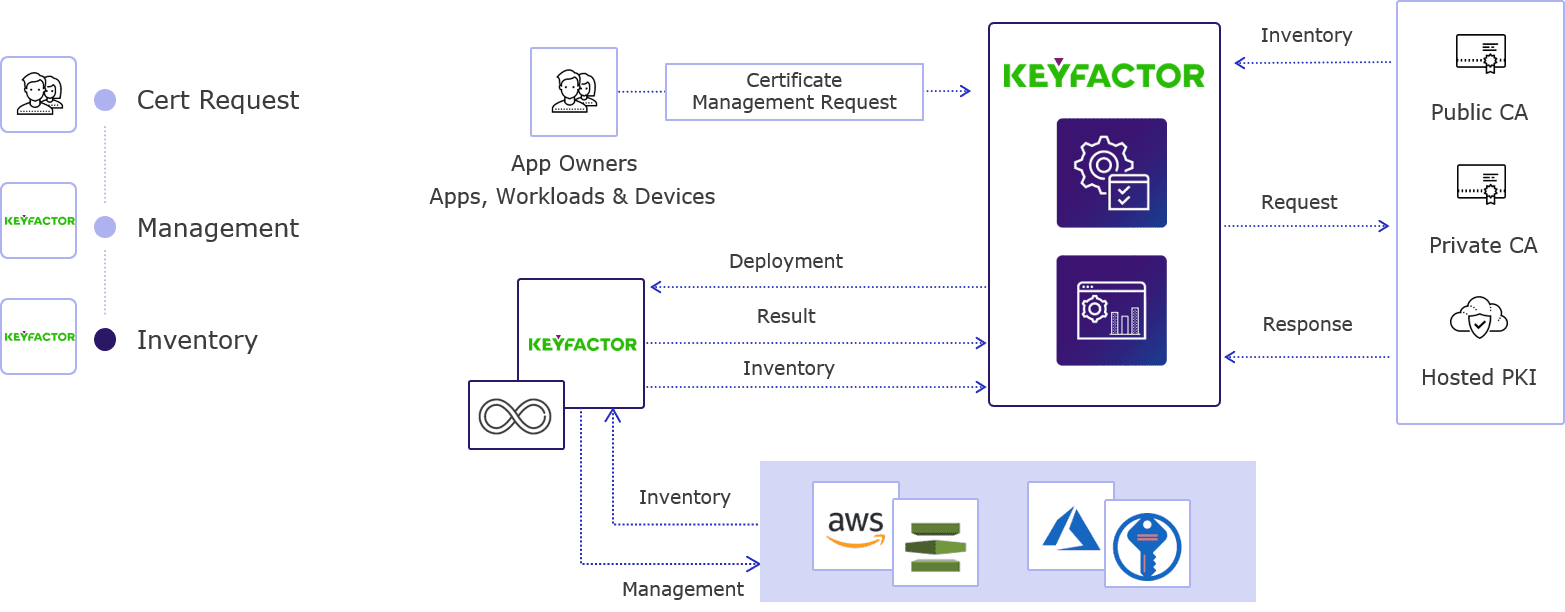
#8 Keyfactor
Domain Est. 1998
Website: keyfactor.com
Key Highlights: Keyfactor is the leader in digital trust and quantum-safe security. Protect every device, workload, AI agent, and connected “thing” with modern PKI, certificate ……
#9 Key
Domain Est. 2013
Website: keyboxsystems.com
Key Highlights: New Key-Box 14. Innovative Key Control Systems. * Secures and locks keys in the cabinet. * Prevent loss of your valuable keys….
#10 Kisi
Domain Est. 2013
Website: getkisi.com
Key Highlights: Kisi is an easy to use cloud based software to manage access to your doors. For physical access use your smartphone’s mobile App or secure badges to unlock ……
Expert Sourcing Insights for Automated Key Management System

H2: 2026 Market Trends for Automated Key Management Systems
The Automated Key Management System (AKMS) market is poised for significant transformation by 2026, driven by escalating cybersecurity threats, stringent regulatory demands, and the rapid expansion of digital infrastructure. Key trends shaping the landscape include:
1. Accelerated Cloud and Hybrid Environment Adoption:
Enterprises are increasingly shifting workloads to cloud and hybrid environments, necessitating AKMS solutions that offer seamless integration across on-premises, public cloud, and multi-cloud platforms. By 2026, cloud-native key management platforms with API-driven architectures will dominate, enabling automated provisioning, rotation, and revocation of cryptographic keys at scale.
2. Integration with Zero Trust and Identity-Centric Security:
As Zero Trust security models become standard, AKMS will play a pivotal role in enforcing strict identity and access controls. Automated key management will be tightly integrated with Identity and Access Management (IAM) systems, ensuring cryptographic keys are dynamically tied to verified user and device identities, reducing the risk of unauthorized access.
3. Rise of Quantum-Resistant Cryptography Preparation:
With the threat of quantum computing advancing, organizations are beginning to prepare for post-quantum cryptography (PQC). By 2026, leading AKMS providers will offer automated tools to manage hybrid cryptographic environments—supporting both classical and quantum-resistant algorithms—and enable smooth migration paths without disrupting operations.
4. Enhanced Automation and AI-Driven Operations:
Automation will extend beyond basic key lifecycle management. AI and machine learning will be embedded into AKMS platforms to predict key rotation needs, detect anomalous access patterns, and auto-remediate policy violations. This shift will reduce operational overhead and improve response times to potential security incidents.
5. Regulatory Compliance as a Growth Catalyst:
Evolving data privacy regulations (e.g., GDPR, CCPA, HIPAA, and emerging global frameworks) will mandate stronger encryption and audit capabilities. Automated key management systems will be critical for maintaining compliance through detailed logging, real-time auditing, and immutable audit trails, driving adoption across regulated industries such as finance, healthcare, and government.
6. Expansion into IoT and Edge Computing:
The proliferation of IoT devices and edge computing environments will create demand for lightweight, automated key management solutions. By 2026, AKMS platforms will support secure, automated key provisioning for resource-constrained devices at the edge, ensuring end-to-end data protection across distributed networks.
In summary, the 2026 AKMS market will be defined by intelligent automation, cloud agility, quantum readiness, and deeper integration with broader security ecosystems—positioning automated key management as a cornerstone of modern data protection strategies.
Common Pitfalls When Sourcing an Automated Key Management System (AKMS)
Quality-Related Pitfalls
Insufficient Validation of System Reliability and Uptime
A key challenge is assuming vendor claims about system availability and fault tolerance without independent verification. Organizations may overlook the importance of real-world performance data, leading to unexpected downtime or maintenance bottlenecks. Always request third-party audit reports, uptime SLAs, and proof of disaster recovery capabilities.
Inadequate Interoperability Testing
Many AKMS solutions fail in heterogeneous environments due to poor integration with existing encryption tools, HSMs, cloud platforms, or legacy systems. Overlooking thorough compatibility testing during procurement can result in costly workarounds or system lock-in.
Poor User Experience and Management Complexity
An AKMS that is difficult to configure, monitor, or audit increases operational risk and the likelihood of mismanagement. Procuring a system without evaluating the administrative interface and automation capabilities may lead to human error and compromised security.
Lack of Scalability and Performance Benchmarking
Organizations often underestimate future key volume and transaction throughput needs. Failing to stress-test the system under projected loads can result in performance degradation as the environment grows.
Intellectual Property (IP)-Related Pitfalls
Unclear Ownership and Licensing of Core Components
Some vendors use open-source cryptographic libraries or third-party modules without transparent licensing terms. This can expose the buyer to legal risks, including patent infringement or restrictive usage clauses that limit deployment or commercial use.
Proprietary Algorithms or Closed-Source Cryptography
Vendors may implement custom or proprietary cryptographic methods not subject to public scrutiny. Relying on such “security through obscurity” undermines trust and may violate compliance standards (e.g., FIPS, Common Criteria), posing long-term security and regulatory risks.
Inadequate Protection of Customer-Generated Keys and Metadata
During procurement, organizations may neglect contractual terms about data ownership. Some AKMS providers retain rights to or access logs of customer key usage patterns, potentially exposing sensitive operational intelligence or violating data sovereignty laws.
Vendor Lock-In Through Proprietary Formats or APIs
AKMS solutions that use non-standard key formats or closed APIs can make migration difficult and expensive. Failing to ensure data portability and API openness in the sourcing process may limit future flexibility and increase dependency on a single vendor.

Logistics & Compliance Guide for Automated Key Management System
This guide outlines the logistics and compliance requirements for the implementation, operation, and maintenance of an Automated Key Management System (AKMS). Adherence ensures security, regulatory compliance, and operational efficiency across all stages of the system lifecycle.
System Deployment and Physical Logistics
Ensure proper planning for the physical installation, transportation, and setup of AKMS hardware. Coordinate with facilities, IT, and security teams to designate secure locations compliant with environmental and access control standards. All equipment must be transported using secure logistics providers with chain-of-custody documentation. Installations must follow manufacturer guidelines and include fail-safes such as redundant power and network connectivity.
Access Control and User Authorization
Define and enforce strict role-based access controls (RBAC) within the AKMS. Only authorized personnel with documented business needs may be granted access. User credentials must be issued through a formal onboarding process, including multi-factor authentication (MFA). Regular access reviews must be conducted quarterly to deactivate or modify privileges based on role changes or departures.
Key Lifecycle Management
The AKMS must support the full cryptographic key lifecycle: generation, distribution, rotation, suspension, backup, recovery, and destruction. Keys must be generated within a FIPS 140-2 or FIPS 140-3 validated cryptographic module. Automated key rotation schedules must align with organizational policy and compliance frameworks (e.g., PCI DSS, HIPAA). Keys must never be stored in plaintext outside the secure module.
Audit Logging and Monitoring
The system must generate comprehensive, tamper-evident audit logs for all key-related activities, including access attempts, key usage, and administrative actions. Logs must include timestamp, user ID, action type, and object affected. Logs must be retained for a minimum of one year or as required by regulations (e.g., SOX, GDPR). Real-time monitoring with alerting for anomalous behavior is required.
Regulatory and Standards Compliance
Ensure AKMS operations comply with applicable regulations and standards, including but not limited to:
– NIST SP 800-57 (Recommendation for Key Management)
– FIPS 140-3 (Security Requirements for Cryptographic Modules)
– GDPR (data protection and encryption requirements)
– HIPAA (for healthcare-related data)
– PCI DSS (for payment card data)
Regular compliance audits must be scheduled, and documentation must be available for inspection.
Incident Response and Key Recovery
Establish a documented incident response plan specific to AKMS events, such as unauthorized access, key compromise, or system failure. Include procedures for immediate key revocation, forensic logging, and notification to relevant stakeholders. Secure, offline key backups must be maintained in geographically separated locations with strict access protocols to support disaster recovery.
Maintenance and System Updates
Schedule regular maintenance, including firmware updates, security patches, and system health checks. All updates must be tested in a non-production environment and deployed during approved maintenance windows. Maintain version control and change logs for all system modifications. Unplanned outages must be reported and investigated per incident management policy.
Training and Awareness
Provide mandatory training for all users and administrators on AKMS policies, secure practices, and their compliance responsibilities. Training must be refreshed annually or when system changes occur. Maintain training records as part of compliance documentation.
Conclusion: Sourcing an Automated Key Management System
In conclusion, sourcing an automated key management system (AKMS) is a strategic imperative for organizations aiming to enhance cryptographic security, ensure regulatory compliance, and streamline operational efficiency. Manual key management processes are error-prone, time-consuming, and increasingly inadequate in the face of growing data volumes and sophisticated cyber threats. An automated solution provides centralized control, secure key lifecycle management, and integration capabilities with existing infrastructure, significantly reducing the risk of data breaches and downtime.
When selecting a vendor, key considerations such as scalability, interoperability, support for industry standards (e.g., PKCS#11, KMIP), audit logging, and cloud-readiness must be evaluated. Additionally, thorough due diligence into the provider’s security certifications, customer support, and long-term viability is essential to ensure a trustworthy partnership.
Investing in a robust, automated key management system not only strengthens an organization’s overall security posture but also future-proofs its cryptographic infrastructure. As data protection regulations evolve and cyber threats grow more complex, automation in key management emerges not just as a best practice, but as a foundational component of modern cybersecurity strategies.